Introduction
From the 19 to the 22 of March, 3 members of our CSIRT Team had the chance to attend the DFRWS EU Conference 2024 held in Zaragoza. The conference showcased cutting-edge research and insights into digital forensics and state-of-the art knowledge in the field.
In this blog post, we’ll provide a summary focusing on subjects that are interesting from the perspective of a CSIRT team and the kind of cases we encountered these days.
Workshops
Forensic deepfake analysis : make your own, and detect if it is real?
The workshop offers hands-on experience in both creating and detecting deepfake images/videos. Participants will learn new methods for generating deepfakes, including face swaps and stable diffusion techniques.
Classic detection methods such as PRNU and double compression detection will be covered, along with discussions on the possibility of hidden messages or watermarks within deepfake videos to aid detection.
The outcome of this workshop shows that it is now very accessible to most of the people, and it will be harder and harder to detect deepfakes for the “normal people” as well as for the already trained professionals. We do think that this will be used more and more as of a Social engineering attack, so we have to be prepared.
DFIR ORC
The DFIR ORC workshop introduces participants to an open-source toolset designed for collecting critical artifacts from Windows machines. It provides hands-on experience in configuring DFIR-ORC for incident response in evidence collection.
Participants learn to customize configurations and use the embedded tool such as FastFind for large-scale indicator searches, DumpIT for full memory acquisition, Yara rules etc.
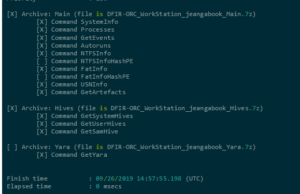
From our point of view, DFIR ORC, part of the open-source DFIR toolset ecosystem, it can be valuable for conducting regular internal security assessments through scheduled deployment (GPO driven). Please note, that the analysis component is not included and must be performed by the user.
The evidence collected are the following:
- FatInfo: Collects FAT metadata from the file system (file names, hashes, authenticode data, etc.)
- FastFind: Locate and report on Indicators of Compromise
- GetSamples: Automated sample collection
- GetSectors: Collects MBR, VBR and partition slack space
- GetThis: Collects sample data from the file system (files, ADS, Extended Attributes, etc.)
- NTFSInfo: Collects NTFS metadata (file entries, timestamps, file hashes, authenticode data, etc.)
- NTFSUtil: NTFS Master File Table inspector
- ObjInfo: Collects the named object list (named pipes, mutexes, etc.)
- RegInfo: Collects registry related information (without mounting hives)
- USNInfo: Collects USN journal
The getting-started workshop is available online: https://dfir-orc.github.io/tuto.html
On Hacknowledge side, we do work with Velociraptor for our daily job for Threat hunting and scalable investigations. This also gives us the possibility to be very reactive, and query some assets in real time to be ingested in our stack to reduce the time to investigate as much as possible.
Small hint for those who read until here, some of our stack will be presented on the Hacknowledge customer board on the 11.06.2024 at the Genev’hack event !
CaseWork!
The main goal of the CASE (Cyber-investigation Analysis Standard Expression) framework is to standardize the exchange of cyber-investigation information. It helps represent various aspects of investigations, like data sources and digital objects, in a consistent way.
CASE is used in different sectors for tasks like information exchange between countries and internal investigations. It aims to make analysis easier, improve compatibility between tools, and maintain the integrity of investigation data.
Source: https://caseontology.org/
The workshop aimed to simplify the process of integrating email and chat message data into the CASE framework. Participants learned how to automatically generate transformation functions using mapping files, convert extracted data into the CASE format, and visualize the resulting CASE graphs.
Once generated, investigators can obtain the kind of relationship graphs, which represent a normalize way in chat conversation:
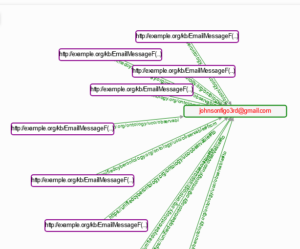

As it is mandatory to correlate most of the data in an investigation, this shows what can be done and how. Please note that this software is not accessible to private companies.
Presentations
Exploring AI in Fraudulent Activities: Unveiling Cybercriminal Tactics
One of the main discussions at the Conference is the usage of artificial intelligence (AI) within fraudulent activities.
The keynote session, led by David Sancho, a Senior Threat Researcher at Trend Micro, provided a comprehensive overview of how cybercriminals are leveraging AI to orchestrate fraudulent actions.
Contrary to popular belief, the adoption of AI in criminal activities predates the recent surge in interest surrounding generative AI. The presentation demonstrates that in underground forums, uncovering the covert discussions surrounding AI technologies and their integration into criminal operations.
Notable examples include FraudGPT, DarkBARD, and DarkBERT, which are believed to function as wrapper services for legitimate AI models like ChatGPT or Google BARD. These tools equip cybercriminals with capabilities ranging from automated phishing scams to the creation of convincing counterfeit content.
Furthermore, the presentation highlighted the emergence of deepfake services tailored for criminal use. While the creation of convincing deepfake videos remains a labor-intensive and costly endeavor, the production of audio deepfakes is significantly more accessible. Consequently posing new challenges for digital forensics practitioners and law enforcement agencies.
Large Language Models and Digital Forensics
One of the highlights of the conference was the exploration of Large Language Models (LLMs) in digital forensics. LLMs models, such as ChatGPT, Mistral or Lama , have emerged as powerful tools for assisting in the analysis and generation of forensic reports.
The presentation from the University of Lausanne shed light on an experiment involving the use of LLMs for writing digital forensic reports.
This experiment underscores the potential of LLMs in automating and assisting during digital forensics or incident response.
DECODE Tool
The ANSSI presentation on the DECODE tool captured the CSIRT team attention. DECODE presents a groundbreaking method for highlight irregularities within executable files. By categorizing PE files on a system based on their degree of anomalies, forensic analysts can efficiently prioritize their investigative efforts during incident response or compromise assessment.
DECODE calculates anomaly scores for PE files through a combination of traditional outlier detection algorithms and graph-based anomaly detection techniques.
Notably, this approach focuses on file metadata, aligning with the mindset of incident response triage, thereby avoiding the necessity for in-depth analysis of binary content. Furthermore, it operates autonomously from pre-trained machine learning models, ensuring flexibility to adapt to changing systems and attack vectors.
The tool is still a POC but :
– a simplified view of the tree structure with the most anomalous PEs
– a Splunk dashboard app which can be integrated into your Splunk platform for results analysis
Source: https://github.com/ANSSI-FR/DECODE/tree/main
The final word
At the dinner event, the DFRWS staff organized a Rodeo, which is a CTF.

The central narrative revolves around the Binary Bandits, a notorious cybercriminal gang disguised as Wild West cowboys and outlaws. During the DFRWS RODEO event, they executed a coordinated assault on the conference network, aiming to sow chaos and pilfer valuable attendee data. Digital investigation teams explored into evidence extracted from Bonnie’s laptop, scrutinizing hard drive data, memory snapshots, and network activity logs to uncover clues about the Binary Bandits’ operations. Their objective was to reveal the gang’s secrets and bring them to justice.
Blue team analysts have the opportunity to enhance their skills in multiple areas during the competition in two hours, so you need to quick and efficient. They can explore Windows artifacts forensics on a disk acquisition. Additionally, they’ll gain insights into potential malware techniques through forensics on volatile memory (Feel free to use Volatility extensively). Furthermore, participants will refine their network analysis skills through network forensics PCAP.
In conclusion, the DFRWS EU Conference 2024 provided valuable insights into the latest trends and advancements in digital forensics. The conference showcased the collective efforts of researchers and practitioners in advancing the field.
While digital forensics and incident response may serve distinct purposes, our CSIRT team remains committed to leveraging these advancements to enhance our incident response capabilities and uphold the security of the digital ecosystem.
The full program of the workshop and conferences are listed here: https://dfrws.org/eu-2024-program/
If you’re interested in having a look on the different services provided by Hacknowledge CSIRT (or just want the badass B’IR sticker), don’t hesitate to contact us at csirt(at)Hacknowledge.ch !

The B’IR Team – Hacknowledge Incident Response



