Hacknowledge Services
Our Services
- Managed detection and response services
- Event monitoring and log management
- IDS and log correlation
- Incident notification & remediation guidance
- Threat intelligence / vulnerability scanning
HACKNOWLEDGE simplifies the complexity of cybersecurity threat detection and response. Our expert security engineers monitor your ICT 24/7 and filter out thousands of events and false-positives. We notify you only when the threat is credible and provide expert guidance for remediation.
Security Is A Matter Of Trust And Honesty
We believe that security should not be driven by fear. Investing in cybersecurity technology can get complex. Many in-house security teams are either understaffed or not well-versed in all the tools purchased. Many times, the technology purchased creates more noise than actionable information. This is where Hacknowledge can help. Our mission is to be your trusted partner by providing our technology and a dedicated team of experts at an affordable price.


We See Ourselves As An Extension Of Your Team
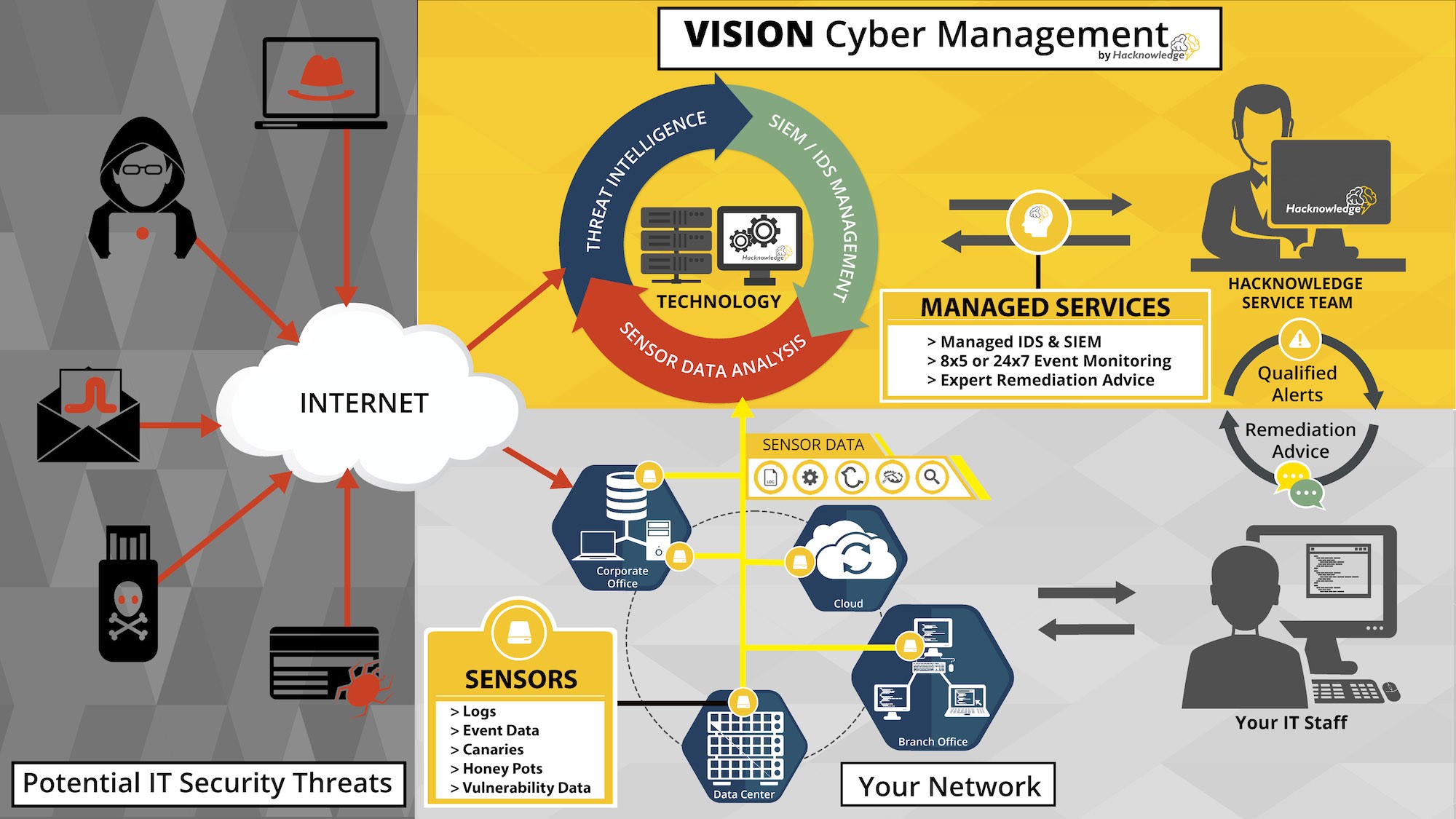
With VISION Cyber Management : we offer a security monitoring service that will help you shorten the time between breach and detection with the ultimate goal of stopping IT threats. We can customize our solution to leverage your existing security devices or tools. Our service is built on experience and intelligence gained from over a decade of penetration testing and mitigating threats.
Searching Your Logs To Find A Breach Is Like Finding A Needle In A Haystack
Filtering through millions of events to find credible threats is the most time-consuming task. We fortify your logs with strong indicators of compromise generated by our custom sensors. These sensors give our engineers the visibility needed to assess anomalies, track trends and detect threats. Each alert is validated and analyzed by our security experts before being sent to you. They will then provide unique insight and advice that machines lack and help you mitigate and respond to the threat.


We Are Much More Than Just A SOC, A SIEM Or A MDR
With VISION Cyber Management : we offer much more than just a SOC, a SIEM or a MDR service. We will help you focus on your business and take the right decisions, select and purchase the right tools, and leverage the use of it. Our interests are aligned with yours . VISION includes : Monitoring, IDS, Sandbox, access to the use case catalog, pentesting, user awareness training & tests … and of course regular meetings and follow-ups with our experts.
Services Diagram
Monitor
Security monitoring and sensing technology for significantly less than the cost of in-house staffing and 3rd party solution fees
Detect
Analysis of activities across your IT assets, reducing thousands of false positive events to just a few high probability alerts
Respond
Immediate alerts when threats are detected and confirmed with professional advice to remediate the intrusion
An all-inclusive, fully integrated Hacknowledge proprietary solution with world-class event monitoring at its core.
Vision Cyber ManagementTM
a HACKNOWLEDGE Cutting-Edge Solution
Indicators Of Compromise (IOC)
Hackers will find ways to evade detection without leaving evidence of compromise. The only way to detect these attacks is to search for signs of covert behavior. This is why we leverage the use of your existing security devices and fortify your logs with strong indicators of compromise generated by our sensors installed on your network. Our technology generates strong signals to identify Indicators of compromise (IOC).
- Using as many sensors as needed
- Identifying known hacking tools/behaviors
- Custom IDS rules linked to threat intel
- Using honeypots
- Monitoring access to files/URL (canaries)
- If needed, exploit the full audit trail
Event Monitoring / Log Management
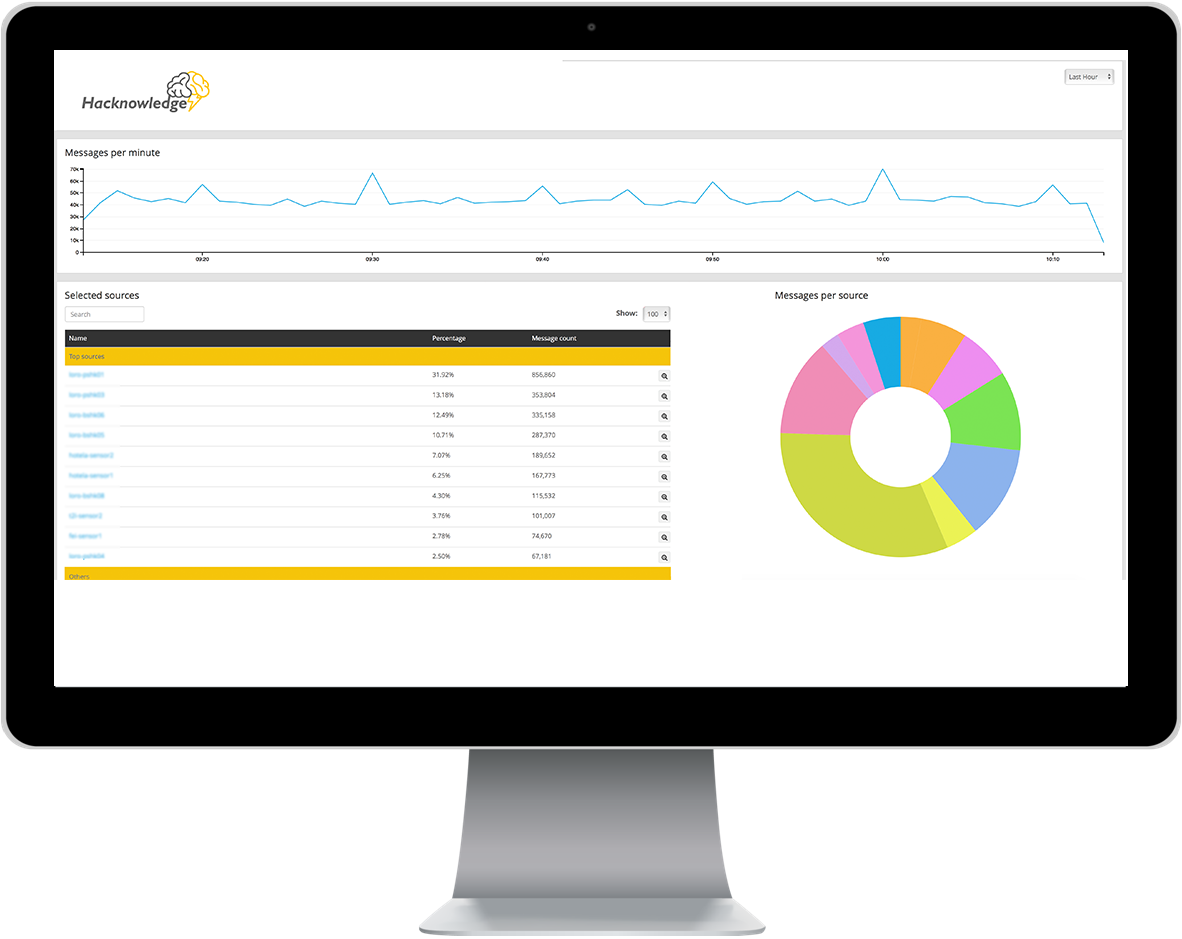
We offer both 24/7 and 8×5 monitoring services. Our team of highly trained security experts monitor and analyze activities across our customers’ IT assets by combining enterprise-class IDS, SIEM, and Log Management technology.
Our team filters down thousands of events and false positives to notify you only when something needs your attention. As a result, your team no longer needs to dig through thousands of alerts or analyze log files to determine what is happening in your IT environment.
Managed IDS / SIEM
No need to invest in expensive and complex IDS and SIEM. Our IDS and SIEM solutions are included with our service. You get security monitoring along with our technology for significantly less than the cost of in-house staffing and paying 3rd party licensing or maintenance fees.
Finally, our experts provide unique insights that machines lack. Before being sent to you, each alert is validated and analyzed by our security-experts who provide you with advice to help you mitigate the threat.

Notification / Remediation
Get immediate alerts when threats are detected along with professional advice and unique insight from our cyber security team to help you mitigate and respond to the threat.
Give your management the visibility they need with real-time security dashboards and recurrent reports. Our dashboards allow you to search and exploit your logs, and get real-time alerts and trends. Our reports summarize the latest alerts and vulnerabilities affecting your company along with your exposure on the Internet.
We Help You Reduce Your Costs
With our solution, there are no complicated plans or a multitude of products to decipher. We believe that security monitoring can be simple and cost-effective. Our one-time cost includes hardware and setup. Our service cost includes software, support, threat intelligence, and security expertise as a single, predictable operating expense.
*VISION Cyber Management by Hacknowledge includes all of the following:
- Managed detection and remediation services
- 24×7 monitoring (8×5 option available)
- Cutting-edge technology (Sensor, IDS, SIEM, sandboxing/file analysis)
- Unlimited vulnerability scanning
- Detect unknown threats, as well as known (signature-based) threats
- Alert and provide expert guidance to remediate threats as they happen
- Analysis of log data and log correlation
- Log aggregation, indexing and search for all your existing devices
- Technology that creates strong indicators of compromise to reduce false positives


