In the ever-evolving landscape of cybersecurity, organizations are continuously seeking ways to enhance their defenses against sophisticated threats.
Traditional approaches like Red Teaming and Blue Teaming have played crucial roles in identifying vulnerabilities and responding to attacks. However, the Purple Teaming approach has emerged as a powerful methodology that bridges the gap between offensive and defensive security strategies.
This blog post will explore the characteristics of the different approaches, the teams involved, the methodology employed, and highlight some notable tools used for emulation and reporting.
Red Teaming Vs Purple Teaming:
Red Teaming primarily focuses on simulating real-world attacks by attempting to breach an organization’s security controls and exploit vulnerabilities. It adopts the role of adversaries and employs various tactics to assess an organization’s defensive capabilities. The primary goal is to uncover weaknesses, provide a comprehensive analysis of risks, and recommend improvements to enhance the security posture as well as challenge the blue Team.
On the other hand, Purple Teaming combines elements of both Red and Blue Teaming. While Red Teams concentrate on offensive techniques, Purple Teaming seeks to collaborate and align the efforts of Red and Blue Teams to a maximum level. The objective is to enhance the overall security level by fostering a continuous feedback loop between the offensive and defensive teams.
Teams Involved in Purple Teaming:
Cyber Threat Intelligence (CTI): CTI teams play a critical role in a Purple Team exercise by providing relevant and timely intelligence on emerging threats, attacker techniques, and vulnerabilities.
Red Team: The Red Team, responsible for offensive security, takes on the role of attackers and employs various tactics to simulate real-world attacks. They aim to emulate the TTPs[1] plan consumed from CTI teamwork.
Blue Team: The Blue Team, responsible for defensive security, focuses on monitoring, detecting, and responding to attacks. They actively engage with the Red Team’s activities, analyze their techniques, and work collaboratively to improve the organization’s security posture.
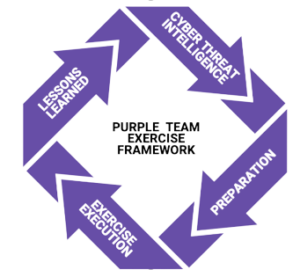
Methodology of a Purple Team Exercise:
Collect: The Purple Team begins by gathering information about the organization’s assets, existing security controls, and threat landscape. They collaborate with the CTI team to understand the latest threats, APT’s[2] and state sponsored groups targeting similar entities.
Build: The Red Team consumes the information collected to develop attack scenarios that align with real-world threats.
Execute: The Red Team executes the planned attacks using manual or automated tools.
Detect: The Blue Team detects, analyzes, and responds to the attacks launched by the Red Team.
Report: After the Purple Team exercise concludes, a detailed report is generated that includes the details executed plan, SOC[3] detection and a lesson learned with all enhancement suggestion.
Technical Aspects:
Plan Execution:
The execution of the plan can be done using manual, automated or hybrid approach. The selection of those tools heavily depends on the scenario to execute, its needs and the offensive security team infrastructure.
In the section below we have chosen to use the automated execution using CALDERA.

Caldera is an open-source framework that allows organizations to create and execute cyber-attack scenarios. It allows the Red Team to emulate various attack techniques and provides valuable insights into an organization’s defensive capabilities.
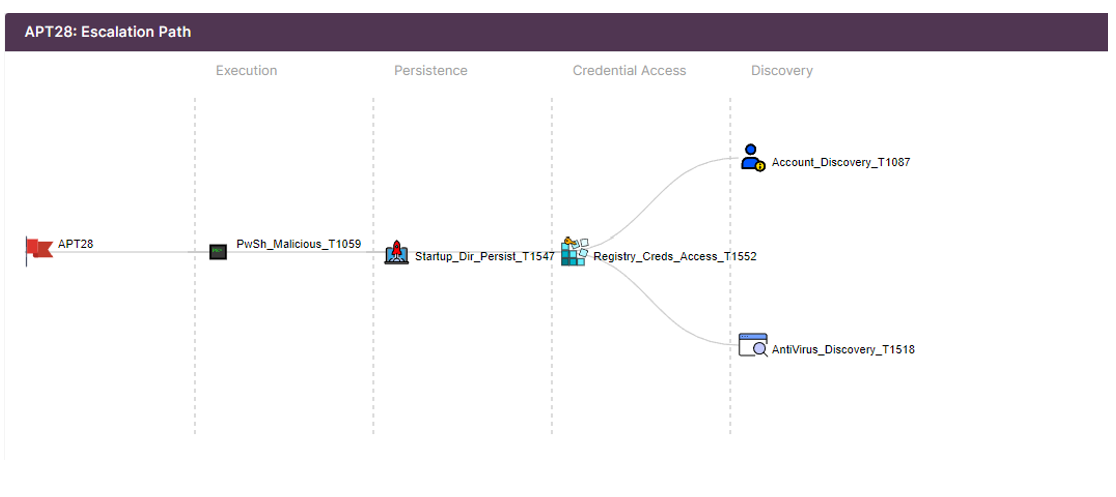
The Red Team will Execute the below plan provided by the Cyber Threat Intelligence Team. [NB: The selected TTPs were randomly chosen to achieve the post.]
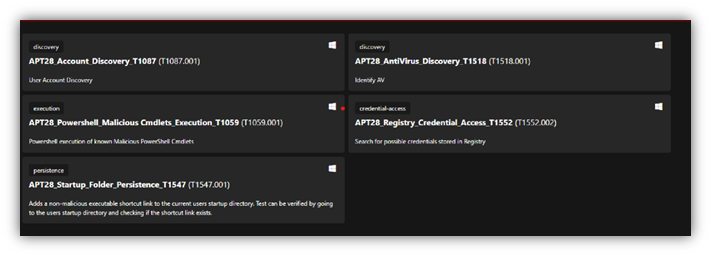
The above created plan needs to be reflected in caldera under Abilities. Offsec team need to create Abilities whish are specific ATT&CK tactic/technique implementation that can be executed on target host along with the command to execute.
The next step would be the creation of Adversary Profile which groups the abilities that need to be executed.
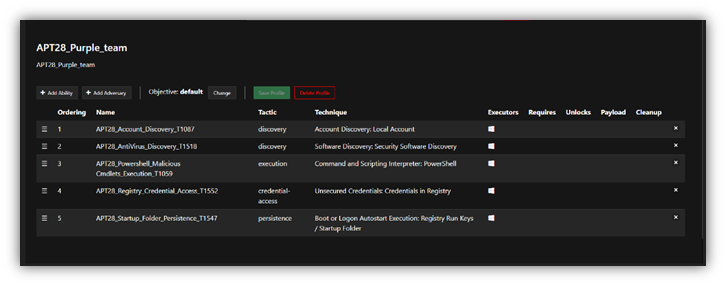
The Last Step on Caldera Side, is to execute the operation which will launch the selected Adversary Profile
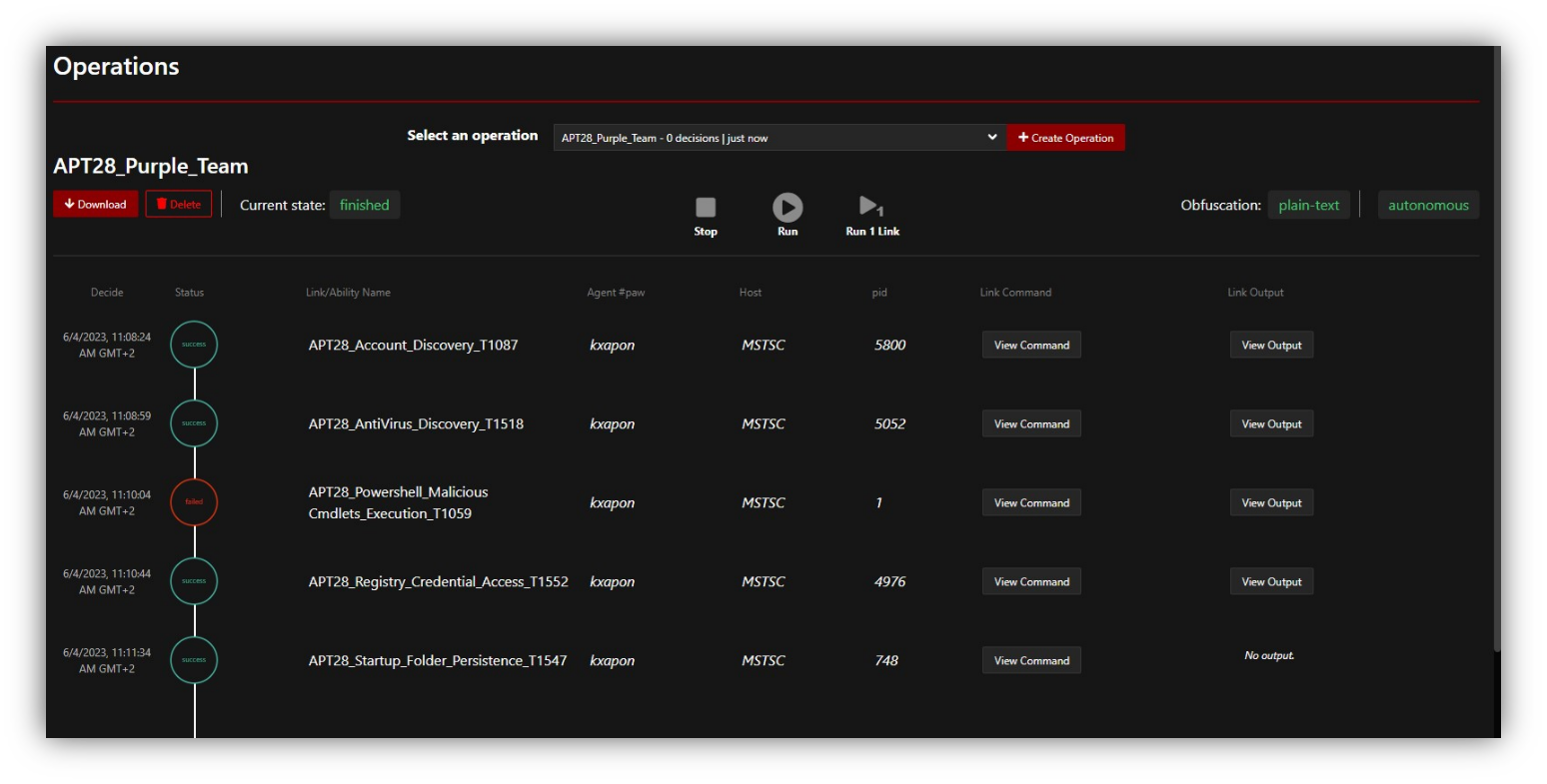
The Plan that got executed and contains 5 techniques launched on the target hosts.
Detection:
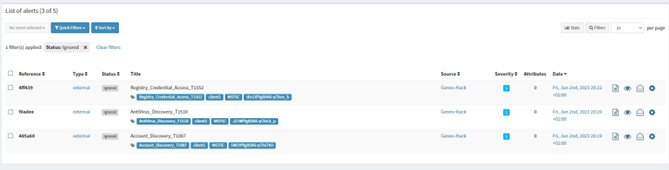
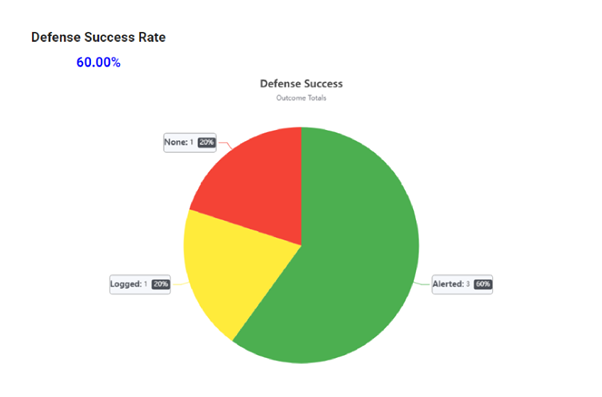
In parallel the Blue Team needs to check his SIEM to double check what Alerts were generated from the APT28 operation plan.
As seen below, the SOC detected 3 out of 5 executions.
Reporting:
The interesting approach in purple Teaming, is this close collaboration between red and blue teams, which is reflected in the adopted approach of Reporting.
VECTR is a tool that facilitates the tracking of your red and blue team testing activities to measure detection and prevention capabilities across different attack scenarios.
The Reporting logic should be as below:
- The Offensive Team Prepare the documentation of his exercise before launching the APT28 Operation
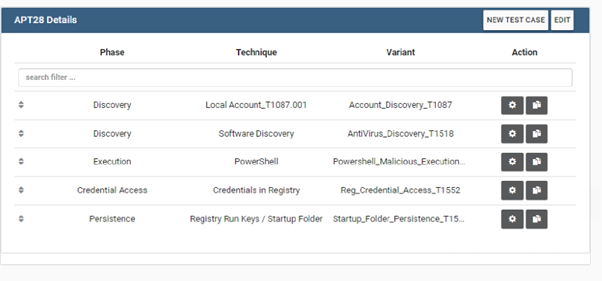
- After Launching the Operation on Caldera, the offensive team need to fill information about the start/End of the execution of each technique.
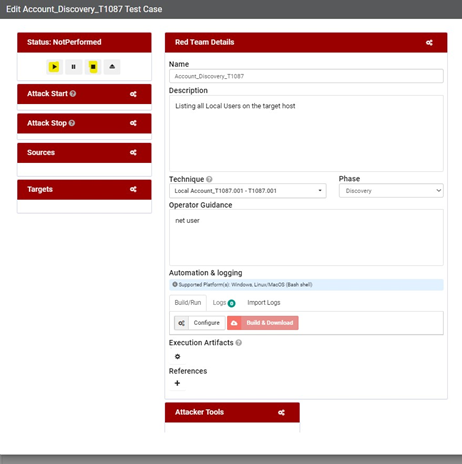
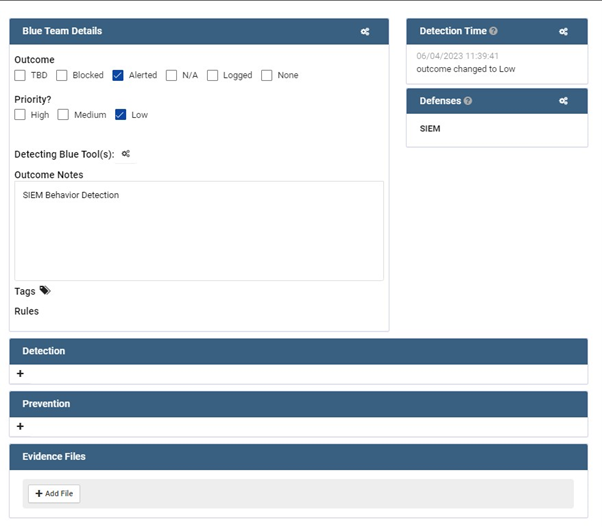
- When the SOC detects any attacks related to the launched emulation plan, they need to fill their part in Vectr.
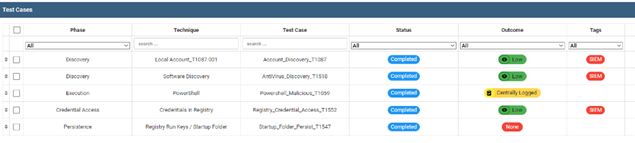
- The output of the full documentation of both blue and Red Team would be:
- Vectr would then allow the creation of multiple report templates that will reflect the output of the executed plan:
Purple Teaming represents a shift in cybersecurity by promoting collaboration between Red and Blue Teams. By combining offensive and defensive strategies, organizations can strengthen their security posture and effectively respond to emerging threats. Through the methodology of collecting intelligence, consuming information, launching emulation plans, and analyzing results, Purple Teams can provide valuable insights and recommendations for enhancing an organization’s defenses. Tools like Caldera and Vectr further empower Purple Teams by facilitating the emulation process and enabling comprehensive reporting.
[1] Tactics, Techniques and Procedures
[2] Advanced Persistent Threat
[3] Security Operation Center
[4] https://scythe.io/library/why-you-should-embrace-purple-team-today



