Introduction
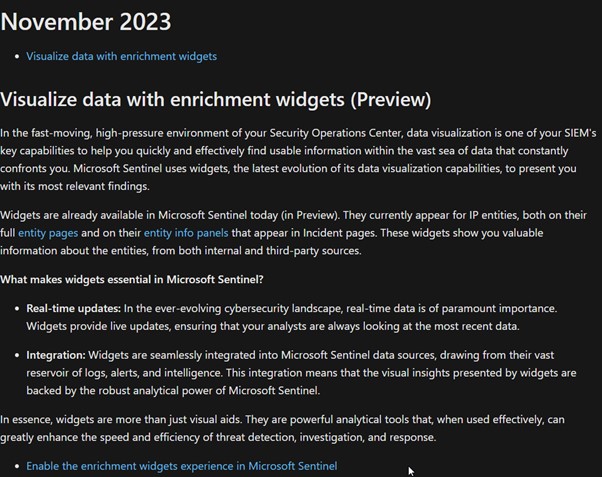
Last week took place Microsoft ignite in Seattle. I was focused on new announcements regarding Sentinel and/or Defender. And the first one who shined in my eyes: the enrichment widget for the UEBA feature in Sentinel🤩.
The promise of this new feature is to empowers security analysts to gain deeper insights into entities by retrieving, visualizing, and understanding additional information. By integrating external content, the enrichment widget elevates data presentation to a new level, enabling analysts to make informed decisions quickly and effectively.
🤔 OK , nice promise, in short a feature which adds more correlation! And that’s good i love the correlation
I’m so curious, let’s try this! First step Let’s navigate to the Entity behavior and find the new preview and the way to configure this new feature:
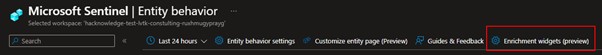
Nice we see that we can connect with 4 sources.
Some sources are well known, such as VirusTotal or AbuseIPDB, and also 2 new tools that I don’t know yet: Recorded future and Anomoli.
Let’s make some research on the web and a little presentation of each one and let’s check if we can use freely and easily this sources.
VirusTotal
VirusTotal is a popular cloud-based malware scanning service that uses a variety of techniques to identify and classify malicious software. The enrichment module can use VirusTotal’s API to retrieve information about files, URLs, and IP addresses. This information can be used to identify potential threats and to prioritize investigations.
Here are some of the benefits of using the VirusTotal API:
- Access to a large database of malware signatures and threat intelligence data
- Ability to scan files, URLs, and IP addresses for malware
- Ability to retrieve detailed information about known malware threats
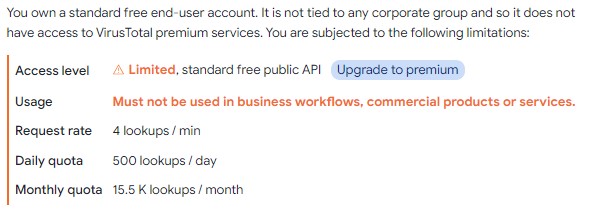
I use it since many years, I I know that we can use it for non business purposes with thus limitation.
Abuse IPDB
AbuseIPDB is a global database of abusive IP addresses. The enrichment module can use AbuseIPDB’s API to retrieve information about IP addresses, such as whether they have been associated with spam, phishing, or other malicious activity. This information can be used to block malicious traffic and to identify potential threats.
Here are some of the benefits of using the AbuseIPDB API:
- Access to a large database of abusive IP addresses
- Ability to check IP addresses against the database in real time
- Ability to block malicious traffic based on IP address
Can also be used for free with limitation
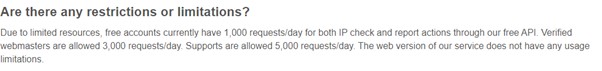
👉https://www.abuseipdb.com/faq.html
Recorded Future
Recorded Future looks like something sponsored by MS, it is a threat intelligence platform that collects and analyzes data from a variety of sources, including public websites, social media, and dark web forums. The enrichment module can use Recorded Future’s API to retrieve information about entities, such as their reputation, associated domains, and social media profiles. This information can be used to identify potential threats and to prioritize investigations.
Here are some of the benefits of using the Recorded Future API:
- Access to a vast amount of threat intelligence data
- Ability to retrieve information about entities from a variety of sources
- Ability to identify potential threats and to prioritize investigations
- 30 days trial available

👉 https://go.recordedfuture.com/microsoft-azure-sentinel-free-trial
Anomali (not tested)
Anomali sounds to be a threat detection and response platform that uses machine learning and AI (very trendy🙃) to identify anomalous activity in network traffic. The enrichment module can use Anomali’s API to retrieve information about network flows, such as their source and destination IP addresses, their protocols, and their payloads like the other platforms. This information can be used to identify potential threats and to investigate security incidents.
Here are some highlights of using the Anomali API:
- Ability to detect anomalous activity in network traffic with AI
- Ability to retrieve information about network flows
- Ability to investigate security incidents
- no trial, no ability to create an account easily…
i will not test this platform, why?, because i don’t like the website, don’t find the information look’s like very complicated to understand how to use it, and you need to contact the sales team for more information…🤦♂️
👉https://www.anomali.com/products/threatstream
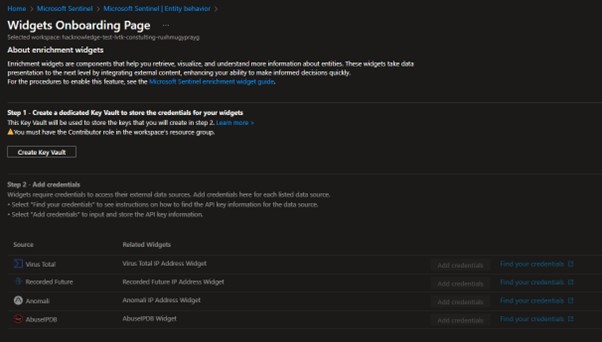
Configuration
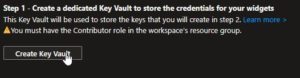
Let’s try to activate the first source, the Step 1 is to create à Key Vault.
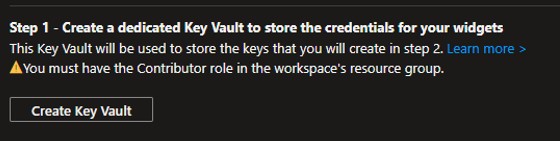
It was to easy, the first error message appeared… asking to register first the subscription with a Key Vault of course. The link provided in the error message doesn’t help… But the message is quite explicit, then let’s try to create a key vault vault for this subscription.
Navigate to Key Vault and create a new key vault for your Lab/Prod/imaginary subscription.
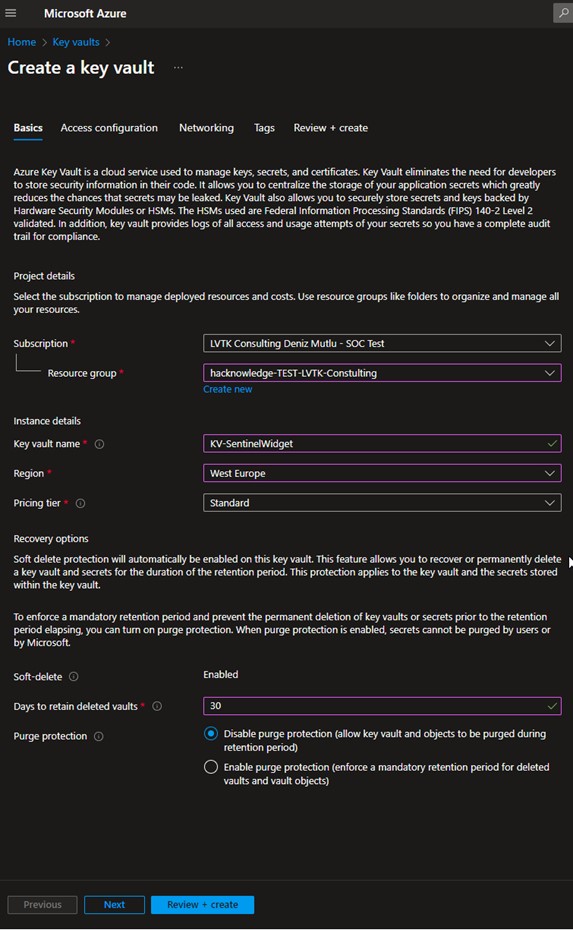
Perfect, deployment in progress

People don’t like to wait sometimes with Azure, but imagine if you do 20 pushups each time that you need to wait 😂

For me it’s always the perfect time for a cup of tea 😍 (and to tease the christmas chocolates for the MSS Team, to check if they read my blog post lol😅)

Ok let’s try again to pass this step 1 to create this dedicated Key Vault for the widgets creds.
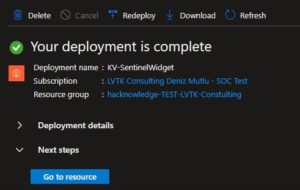
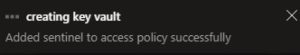
Better, we can now pass to step 2 and add the API key for the different sources. let’s start with the VirusTotal, from my VirusTotal account , I retrieve the Api Key and try to follow the wizard to add the credentials.
 I select my subscription/RG and just renamed the Key Vault random name, by something more “eyes friendly”, with some doubts about this super idea…
I select my subscription/RG and just renamed the Key Vault random name, by something more “eyes friendly”, with some doubts about this super idea…
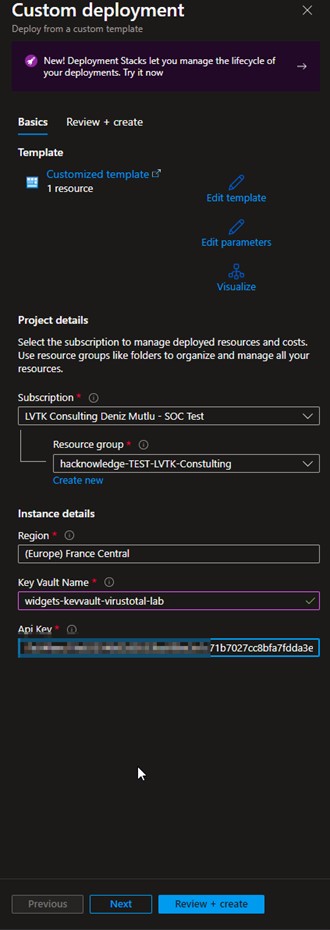
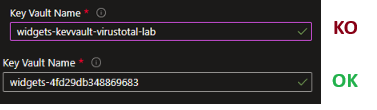
It was too easy… and second error, I renamed the Key Vault Name.. and Azure don’t like this,
![]()
Don’t edit the random custom name of the “Key Vault Name” just close your eyes😉 and it’s works better. Keep in mind that Key Vault names, and some other objects names in Azure, should be universally unique and are accessed by URI it’s why sometimes it’s not a good idea to rename, but in this case i don’t undestand why they checked “passes” for the name…
The first source is successfully added 🎉, let’s continue with AbuseIPDB, from my account i create and copy the API key and add to the Enrichment Widget using the custom deployment wizard like the previous one, and without touching the name generated for the Key Vault this time.
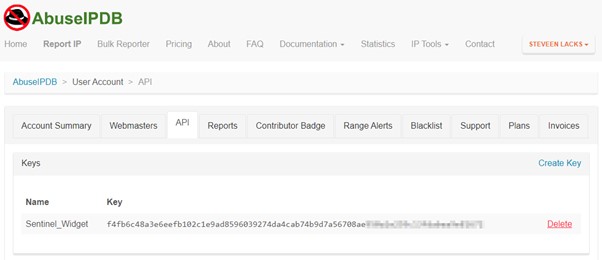
Great, for Recorded Future, you need to wait…I’m still waiting for the API Key. I don’t want to drink a thousand teas or do some pushups, then i will add this source as the same manner of the previous for the part 2 of this article.
Conclusion
OK and now? With the enrichment widget configured, I eagerly await the first results to fully assess its effectiveness. In the upcoming Part 2 of this article, I’ll delve into the practical application of the enrichment widget, showcasing its capabilities and providing a comprehensive evaluation. Stay tuned to discover how the enrichment widget enhances Microsoft Sentinel UEBA and transforms your threat hunting experience. (or not 😜)
If you wan to learn more about this new preview feature:👇
Visualize data with enrichment widgets in Microsoft Sentinel | Microsoft Learn

Deniz Mutlu | Principal Cloud Engineer / MCT
If you want to contact me here is my linkedin